CAMBRIDGE, Mass., Feb. 25, 2022 (GLOBE NEWSWIRE) -- The APWG's new Phishing Activity Trends Report reveals that APWG saw 316,747 phishing attacks in December 2021 — the highest monthly total observed since APWG begain its reporting program in 2004. Overall, the number of phishing attacks has tripled from early 2020.
The full report is available here:
https://docs.apwg.org/reports/apwg_trends_report_q4_2021.pdf
In the fourth quarter of 2021, APWG founding member OpSec Security found that the financial sector, which includes banks, became the most frequently attacked cohort, accounting for 23.2 percent of all phishing. Attacks against webmail and software-as-a-service (SaaS) providers remained prevalent as well. Phishing against cryptocurrency targets — such as cryptocurrency exchanges and wallet providers — inched up to represent 6.5 percent of attacks.
Overall, the number of brands that were attacked in 4Q descended from a record 715 in September 2021, cresting at 682 in November for the Q4 period.
Abnormal Security observed 4,200 companies, organizations, and government institutions falling victim to ransomware in Q4 2021, some 36 percent higher than in Q3 2021 and the highest number the company has witnessed over the past two years. "The overall distribution of ransomware victims indicates that ransomware attacks are industry-agnostic," said Crane Hassold, Director of Threat Intelligence at Abnormal Security.
"Like with other financially-motivated cyber-attacks, the focus of most ransomware attacks is more about the ability to quickly profit from the exploitation of a corporate network and less about the characteristics of the victim company itself." The top industries impacted by ransomware in Q4 2021 were manufacturing, retail & wholesale, business services, construction, and healthcare.
PhishLabs, by HelpSystems, analyzed malicious emails reported by corporate users and categorized them by threat type. PhishLabs found that in Q4 2021: 51.8 percent of them were credential theft phishing attacks; 38.6 percent were response-based attacks (such as BEC, 419, and gift card scams); and 9.6 percent were malware delivery attacks.
Agari by Helpsystems found that the average amount requested in wire transfer BEC attacks in Q4 2021 was $50,027, down from $64,353 in Q3 2021. This decrease was because scammers requested fewer big-dollar transfers over $100,000. RiskIQ also observed a surge in phishing continued along with an increase in the overall number of phishing emails And Axur found that phishing in Brazil went down in Q4, a pleasantly surprising development during the holiday shopping season.
Agari found that domain name registrar NameCheap was the primary registrar used by cybercriminals to register the domain names for BEC attacks in 4Q 2021. NameCheap accounted for more than half of all BEC domain registrations, with Google and GoDaddy each making up 8 percent. As the name implies, NameCheap is one of the least expensive places to register a domain. This is likely a factor in its popularity with scammers.
RiskIQ found that the 13,947 confirmed phishing URLs reported to APWG in Q4 2021 were hosted on just 1,444 unique second-level domains. In comparison, in Q3 RiskIQ analyzed 4,340 confirmed phishing URLs and found that they were hosted on 2,649 unique second-level domains — almost twice as many domains.
The full report is available here:
https://docs.apwg.org/reports/apwg_trends_report_q4_2021.pdf
Trends Report Resource Note for Researchers: With this edition of the Trends Report, APWG adds metrics for ransomware attacks [p. 6] and malicious email types [p. 10].
Abnormal Security's ransomware metrics provide insight into the industry verticals that are being subject to ransomware attacks, the relative intensity of attacker interest for each one and, as importantly, the revenue-echelon of victim enterprises that are the focus of ransomware gangs' interest. This knowledge helps organizations' managers, curators and security vendors better understand their overall risk for being subject to ransomware attack.
PhishLab's metric for email attacks segments the categories into threat types (credential theft; response-based attacks; and malware delivery) to bring insight into the nature of cybercrime attacks directed against enterprise users. Historically, Trends Report focused on consumer-targeted phishing attacks employing social-engineering based phishing attacks that abused brands — but, for full-spectrum understanding of user risks at work and at home, PhishLab's metric measures the kinds of email threat types experienced by enterprise users.
Trends Report Correction Note: Due to a transcription error, an early edition of the Q3, 2021 Trends Report, published 22 November 2021, indicated that attacks against financial institutions and payment providers combined accounted for 34.9 percent of attacks in the quarter when the actual and correct percentage should have been reported as 24.9 percent. The corrected Q3, 2021 report is available here: https://docs.apwg.org/reports/apwg_trends_report_q3_2021.pdf All previous APWG Trends Report editions from January, 2004 onward, are available in this directory - https://apwg.org/trendsreports/ - as a service to industry, government, multilateral organizations and the general public.
Media Contacts
For media inquiries related to the APWG, please contact APWG Secretary General Peter Cassidy (pcassidy@apwg.org, +1.617.669.1123). Or for company-specific content related to this release, please contact:
Anil Prasad at Abnormal Security (www.abnormalsecurity.com/contact),
Stefanie Wood Ellis of OpSec Security (sellis@opsecsecurityonline.com);
Rachel Woodford of Agari (Rachel.Woodford@helpsystems.com);
Eduardo Schultze of Axur (eduardo.schultze@axur.com,+55 51 3012-2987);
Stacy Shelley of PhishLabs (stacy@phishlabs.com, +1.843.329.7824);
Holly Hitchcock of RiskIQ (holly@frontlines.io).
About the APWG
Founded in 2003, the Anti-Phishing Working Group, (APWG) is the global industry, law enforcement, and government coalition focused on unifying the global response to electronic crime. Membership is open to qualified financial institutions, online retailers, ISPs and Telcos, the law enforcement community, solutions providers, multilateral treaty organizations, research centers, trade associations and government agencies. There are more than 1,800 companies, government agencies and NGOs participating in the APWG worldwide. The APWG's www.apwg.org and education.apwg.org websites offer the public, industry and government agencies practical information about phishing and electronically mediated fraud as well as pointers to pragmatic technical solutions that provide immediate protection. The APWG is co-founder and co-manager of the STOP. THINK. CONNECT. Messaging Convention, the global online safety public awareness collaborative and founder/curator of the Symposium on Electronic Crime Research, the world's only peer-reviewed conference dedicated specifically to electronic crime studies. APWG advises hemispheric and global trade groups and multilateral treaty organizations such as the European Commission, the G8 High Technology Crime Subgroup, Council of Europe's Convention on Cybercrime, United Nations Office of Drugs and Crime, Organization for Security and Cooperation in Europe, Europol EC3 and the Organization of American States. APWG is a member of the steering group of the Commonwealth Cybercrime Initiative at the Commonwealth of Nations. Among APWG's corporate sponsors are: Abnormal, Accenture, Acronis, Afilias, AGARI, AhnLab, AT&T, Allure Security, AREA 1, AIT, appgate, Avast, Awayr AI, AXUR, BW CIRT, Bambenek Consulting, Banelco CSIRT, Bolster, BrandShield, Browlser, ByteDance, Canva, CaixaBank, Check Point, Cisco, CLARO, Cloudflare, CLOUDMARK, COFENSE, Coinbase, Comcast, CSC, CSIRT BANELCO, CSIS, Cyan Digital Security, CYREN, Cyxtera, CZ.NIC, DigiCert, DNS Belgium, DomianTools, EBRAND, Entrust Datacard, ESET, Facebook, FirstRand, Fortinet, FraudWatch, GetResponse, GMS Securidad, GoDaddy Registry, Group-IB, Guidewire. Hitachi Systems, .ID, ICANN, Infoblox, Ingressum, IQ Global, iThreat, Kaspersky, KnowBe4, Lenos Software, LINE, Looking Glass, LSEC, Mailshell, McAfee, Microsoft, Mimecast, NAVER, Netcraft, NetSTAR, Noblis, Nominet, Opera, OpSec Security, Palo Alto Networks, PANDI, PayPal, PhishLabs, Proofpoint, Qintel, Rakuten, Recorded Future, Red Sift, REDIRIS, ReversingLabs, RiskIQ, RSA, S2W Lab, SafeGuard Cyber, Salesforce, Secutec, SIDN, SlashNext, Sopos, SWITCH, Symantec, Thomsen Trampedach, ThreatSTOP, TNO, TrendMicro, Trustwave, Twilio, Unbiased Security, Vade, Verisign, Viettel Cyber Security, Webroot, workday, ZeroFOX, ZibaSec, ZIX, and zvelo.
Related Images
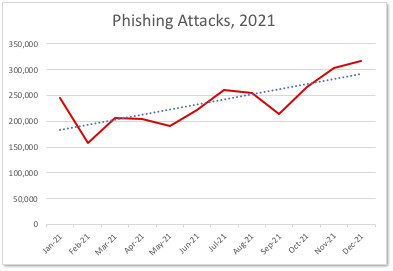
Image 1: Phishing Hits All-Time High in December 2021
Phishing Hits All-Time High in December 2021
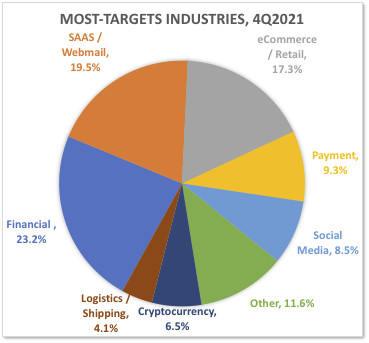
Image 2: Most-Targeted Industries for Phishing in Q4 2021
Most-Targeted Industries for Phishing in Q4 2021
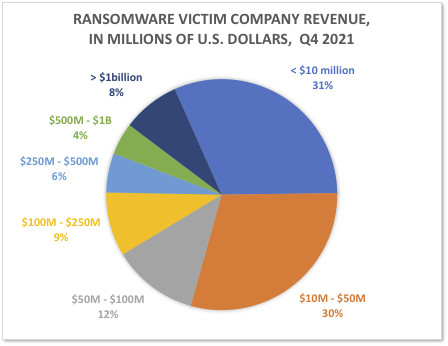
Image 3: Ransomware Victim Company - By Revenue Echelon in Q4 2021
Ransomware Victim Company - By Revenue Echelon in Q4 2021
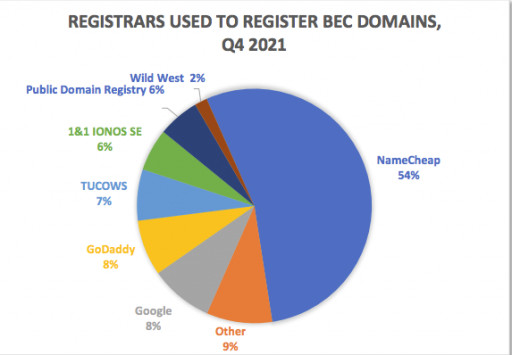
Image 4: Registrars to Register BEC Domains in Q4 2021
Registrars to Register BEC Domains in Q4 2021
This content was issued through the press release distribution service at Newswire.com.
Attachment
