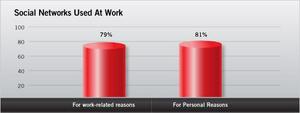
-- 79% of employees use social media (Facebook, LinkedIn, YouTube) at
work for business reasons and 51% access social media sites at least once
per day.
-- IT managers reported an average of 34 security and data leakage
incidents per month.
-- 73% of IT managers report at least one security incident as a result
of Internet application usage; viruses, Trojans and worms (59%) are most
common, followed by spyware (57%) for a close second.
-- 37% of companies report an instance of non compliance with corporate
or regulatory policy, while 27% report incidents of accidental or
unintentional data leakage.
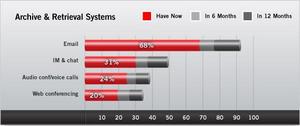
-- Despite the new Federal Rules for Civil Procedure, only 31 percent of
enterprises store IM communications. One in four has copies of audio
conferences (25%), while slightly fewer (20%) archive corporate Web
conferences.
Unified Communications
Unified communications suites, such as Microsoft Office Communications
Server and IBM Lotus Sametime, are becoming integral to the way employees
work today. However, IT managers are finding that their UC rollouts don't
significantly reduce employee use of consumer-oriented Web 2.0 applications
and public instant messaging networks. Security and compliance controls
must extend across all UC modalities in this heterogeneous environment,
both enterprise-sanctioned and consumer-oriented.
Unified communications suites, which give enterprises a way to enable
employees with multiple communications modalities over an IP
infrastructure, exist today at about 29 percent of IT respondent
organizations and an additional ten percent have deployed pilots to a
limited number of users. Security, compliance and management issues are top
of mind among IT managers in organizations with UC deployed.
The full report, "The Collaborative Internet: Usage Trends, Employee
Attitudes and IT Impact," is available from FaceTime Communications at
www.FaceTime.com/survey08/summary.
FaceTime's Solutions for the New Internet
Because these collaborative Internet applications pose myriad network and
information security risks, the heterogeneous network environment that they
create must be understood, secured and managed by IT.
FaceTime's
Unified Security Gateway (USG) is a secure Web gateway appliance that
enables enterprises to control these real-time communications. USG
integrates management, security and compliance of Web and Web 2.0
communications, consumer-driven applications such as public IM, Skype and
P2P, and enterprise-class unified communications suites such as Microsoft's
Office Communications Server and IBM Lotus Sametime. From a single
platform, organizations can enable and enforce safe and productive use of
these applications and protect the network against inbound malware,
mitigate information leakage risks and insure that corporate, regulatory
and e-discovery needs are met.
About FaceTime Communications
FaceTime Communications enables the safe and productive use of instant
messaging, Web usage and unified communications platforms. Ranked number
one by IDC for four consecutive years, FaceTime's award-winning solutions
are used by more than 900 customers for security, management and compliance
of real-time communications. FaceTime supports or has strategic
partnerships with all leading public and enterprise IM network providers,
including AOL, Google, Microsoft, Yahoo!, Skype, IBM and Jabber.
FaceTime is headquartered in Belmont, California. For more information
visit http://www.facetime.com or call 888-349-FACE. The FaceForward blog,
at http://blog.facetime.com, offers thoughts and opinions about the
changing nature of Internet
FaceTime, FaceTime Communications, IMAuditor, GEM, Facetime Unified
Security Gateway, FaceTime Security Labs, IMPact Index, SpywareGuide.com
and the FaceTime logo are registered trademarks and trademarks of FaceTime
Communications, Inc. Other trademarks and registered trademarks are the
property of their respective owners.
Contact Information: FaceTime Media Contact: Emily Chamberlin A&R Edelman 650-762-2945